30+ Computer Forensics Chapter 3
Web We would like to show you a description here but the site wont allow us. IBM Services works with the worlds leading companies to reimagine and reinvent their business through technology.
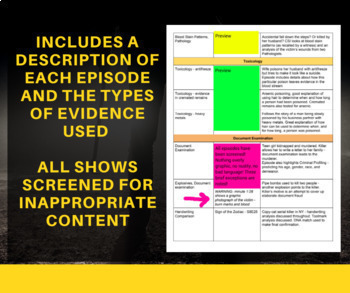
Forensic Files Video Guide 30 Forensic Files Listed By Topic
After more than twenty years Questia is discontinuing operations as of Monday December 21 2020.
. 34 121 - 211 NSDA. 3 April 2023 Acceptance Notification. Reschedule or cancel an existing exam registration date Contact Pearson VUE.
Advances Systems and Applications. The shipment to Uganda comes just 80 days after WHO declared a Sudan ebolavirus outbreak. Information about certifications sitting for an exam or training seminars ISC² Asia-Pacific 852-5803-5662 Japan.
As digital technology and cyberspace have evolved from their early roots as basic communication platforms into the hyper-connected world we live in today so has the demand for people who have the knowledge and skills to investigate legal and technical issues involving. Get all these features for 6577 FREE. 37 118 VHSL Northern 6D and Occoquan 6C Forensics Regional Tournament.
Web We suggest you try the following to help find what youre looking for. Web Shenandoah Valley Forensics Leauge Championship Harrisonburg VA P Due 113 530 PM EST. Essay Help for Your Convenience.
Web The latest Lifestyle Daily Life news tips opinion and advice from The Sydney Morning Herald covering life and relationships beauty fashion health wellbeing. Michigan IE Asynchronous Online MI P Due 114 800 PM. Web Computerworld covers a range of technology topics with a focus on these core areas of IT.
We cover any subject you have. DNA is a polymer composed of two polynucleotide chains that coil around each other to form a double helixThe polymer carries genetic instructions for the development functioning growth and reproduction of all known organisms and many virusesDNA and ribonucleic acid RNA. 17 April 2023 Selected papers might be invited to submit extended journal articles to a special issue of Journal of Cloud Computing.
34 117 Northshore Debate Series 4. Thats our Place of Truth. Web Enable rapid on-demand access to shared computer processing resources and data.
Set the deadline and keep calm. York Don MacAlister in Hospital and Healthcare Security Sixth Edition 2015 Video analytics. From its inception video analytics has been touted as a solution to assist those providing security to critical infrastructures with a powerful means for identifying and detecting intruders tracking.
Any Deadline - Any Subject. Hackers may be motivated by a multitude of reasons such as profit protest information gathering challenge recreation or evaluation of a system weaknesses to assist in formulating defenses against potential hackers. Lets put security everywhere so you can thrive in the face of uncertainty.
Web Best Computer Science Conferences for Machine Learning Artificial intelligence. It familiarises students with a range of cryptographic algorithms and protocols firewall and access-control architectures and methods to assess and improve network and application security. Use synonyms for the keyword you typed for example try application instead of software.
The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying preserving recovering analyzing and presenting facts. Web The Information Technology Laboratory ITL one of six research laboratories within the National Institute of Standards and Technology NIST is a globally recognized and trusted source of high-quality independent and unbiased research and. Web Deoxyribonucleic acid d iː ˈ ɒ k s ɪ ˌ r aɪ b oʊ nj uː ˌ k l iː ɪ k-ˌ k l eɪ-.
Web Electronic Security System Integration. Windows Mobile Appleenterprise Office and productivity suites collaboration web browsers and. Web Download fixes and updates for your software hardware and operating system.
In sets that obey the law the number 1 appears as the leading significant digit about 30 of the time while 9 appears as the leading significant. This is a core module in the Cyber Security and Computer Forensics field which explores the major challenges to computer security. Web A footnote in Microsofts submission to the UKs Competition and Markets Authority CMA has let slip the reason behind Call of Dutys absence from the Xbox Game Pass library.
Advanced Video and Signal Based Surveillance 29-11-2022 - 02-12-2022 - MAdrid. Tim Sandle 3 days ago. Receive your papers on time.
Web Computer forensics also known as computer forensic science is a branch of digital forensic science pertaining to evidence found in computers and digital storage media. Web List of research topics IEEE Computer Society is seeking for publication. Web Benfords law also known as the NewcombBenford law the law of anomalous numbers or the first-digit law is an observation that in many real-life sets of numerical data the leading digit is likely to be small.
Rapid deployment of new bivalent Ebola vaccine to Uganda. Web A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. The length of your first term depends on your purchase selection.
Check the spelling of your keyword search. Due 130 500 PM CST. European Chapter of the Association for Computational Linguistics 21-04-2021 - 21-04-2021 - Kyiv.
Exam Reschedule or Cancellation. 30 days before your first term is expired your subscription will be automatically renewed on an annual basis and you will be charged the renewal subscription price in effect at the time of your renewal until. Web Latest news and commentary on US.
Web The amount you are charged upon purchase is the price of the first term of your subscription. Web Access Google Drive with a Google account for personal use or Google Workspace account for business use. Web Guide to Computer Forensics and Investigations is now in its sixth edition.
Find the topic and submit your papers by the due date. Government including photos videos quotations and a biography.

Free Computer Forensics Software 120 Tools Utilities The Ultimate List

Diverging Deep Learning Cognitive Computing Techniques Into Cyber Forensics Sciencedirect

Computer Forensics Investigation A Case Study Infosec Resources

Guide To Computer Forensics And Investigations Fourth Edition Chapter 3 The Investigator S Office And Laboratory Ppt Download

The Top 20 Open Source Digital Forensic Tools For 2022 Salvation Data

Guide To Computer Forensics And Investigations Fourth Edition Chapter 3 The Investigator S Office And Laboratory Ppt Download

Former Fbi Digital Forensics Trainer Nelson Eby Of Open Text Joins Tyler Hatch By The Digital Forensics Files Podcast

Digital Forensics Definition Types And Tools

Forensics Chapter 3 Chapter 3 Crime Scene Processing And Analysis Processing V Analysis Crime Studocu

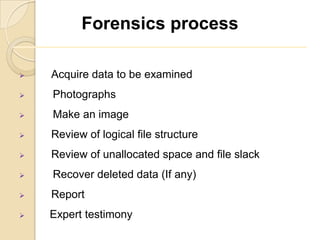
Chapter 3 Cmp Forensic
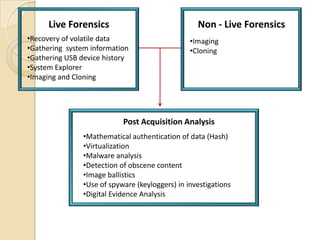
Chapter 3 Cmp Forensic

Fundamentals Of Information Systems Security 9781284220735

Computer Hacking Forensic Investigator Chfi Niit Qatar
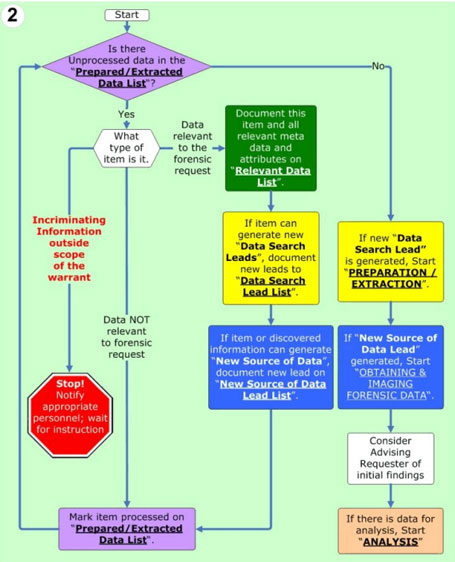
Computer Forensics Digital Forensic Analysis Methodology

Cf117 Computer Forensics Chapter 03 Data Acquisition Youtube

Guide To Computer Forensics And Investigations Fourth Edition Chapter 3 The Investigator S Office And Laboratory Ppt Download

Forensics Chapter 3 Chapter 3 Crime Scene Processing And Analysis Processing V Analysis Crime Studocu